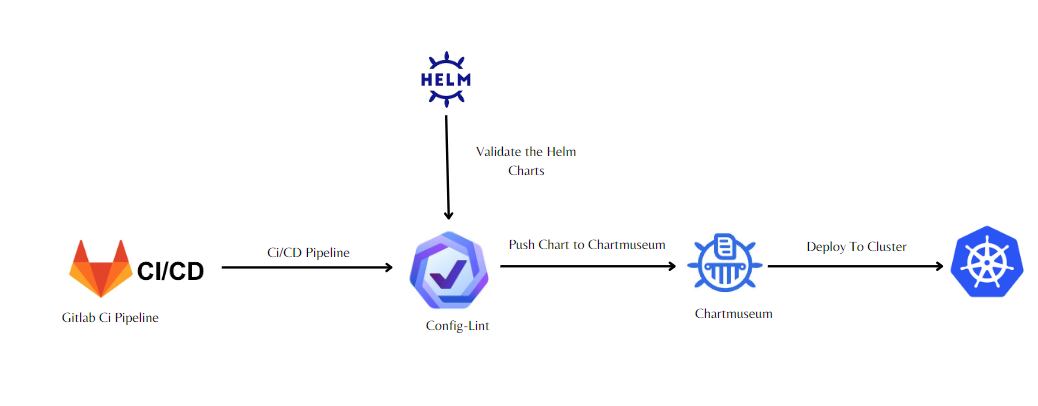
Introduction
Config-lint is a powerful command-line tool designed to streamline the validation of Kubernetes configuration files. By leveraging rules specified in YAML, Config-lint ensures adherence to best practices, security standards, and custom policies. This tool is indispensable for integrating into Continuous Integration and Continuous Deployment (CI/CD) pipelines, allowing seamless validation of configuration changes before deployment.
Integrating Config-lint into CI/CD Pipelines
One of the key benefits of Config-lint is its seamless integration into CI/CD pipelines. By incorporating Config-lint as a step in your pipeline, you can automatically validate Kubernetes configuration files before deployment. This ensures that only compliant configurations are promoted to production environments, reducing the risk of misconfigurations and potential downtime.
Custom Rules with YAML
Config-lint allows users to define custom rules using YAML configuration files. This flexibility enables organizations to enforce specific standards and policies tailored to their environment. Whether it's enforcing naming conventions, resource limits, or security policies, Config-lint's YAML-based rules empower teams to maintain consistency and compliance across Kubernetes configurations.
Validating Helm Charts
In addition to standalone configuration files, Config-lint can also validate Helm charts. Helm is a popular package manager for Kubernetes, and ensuring the integrity of Helm charts is crucial for smooth deployments. With Config-lint, teams can validate Helm charts against predefined rules, ensuring that charts adhere to best practices and organizational standards.
Config-lint simplifies Kubernetes configuration validation by providing a flexible and intuitive toolset. By integrating Config-lint into CI/CD pipelines and leveraging custom YAML rules, organizations can ensure the reliability, security, and compliance of their Kubernetes deployments. With support for Helm charts validation, Config-lint offers a comprehensive solution for maintaining consistency and best practices across Kubernetes environments. Start using Config-lint today to streamline your Kubernetes configuration validation process and elevate your CI/CD workflows to the next level of efficiency and reliability.
Integrating Config-lint into Giltab CICD
1) Docker File for Creating Image which I Will use in Pipeline
root@master:~# cat Dockerfile
FROM ubuntu:latest
MAINTAINER omvedi25@gmail.com
ADD config-lint /usr/local/bin/
ADD helm /usr/local/bin/
2- Build the image and push it to Artifact
root@master:~# docker build -t omvedi25/config-lint:v1.1 .
root@master:~# docker push omvedi25/config-lint:v1.1
3- Create a gitlab-ci.yaml pipeline
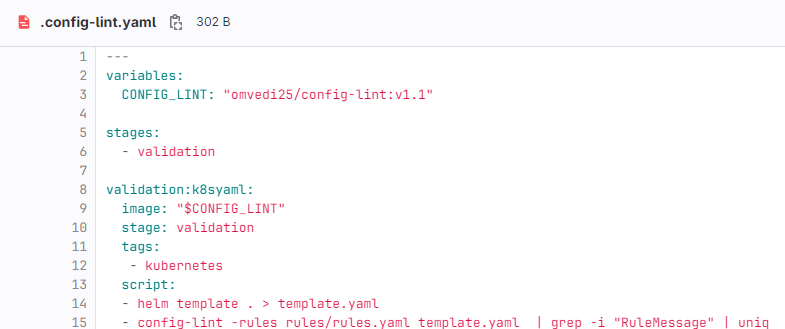
4- Create a project for helm Chart
5- Lets Create rules.yaml file putting rules into it which will get validate before pushing the chart to chartmuseum.
version: 1
description: Rules for Kubernetes spec files
type: Kubernetes
files:
- "*.yaml"
rules:
- id: POD_RESOURCE_REQUESTS_LIMITS
severity: FAILURE
message: Containers in Pod must specify both resource requests and limits
resource: Pod
assertions:
- key: spec.containers[*].resources.requests
op: notPresent
- key: spec.containers[*].resources.limits
op: notPresent
match: any
tags:
- pod
- id: DEPLOYMENT_RESOURCE_REQUESTS_LIMITS
severity: FAILURE
message: Containers in Deployment must specify both resource requests and limits
resource: Deployment
assertions:
- key: spec.template.spec.containers[*].resources.requests
op: notPresent
- key: spec.template.spec.containers[*].resources.limits
op: notPresent
match: all
tags:
- deployment
The above rule will check in the chart for deployment that resource request and limits are mentioned or not.
6- Create gitlab-ci.yaml to run the validation on the charts
---
include:
- project: 'guilds1/cloud-native-guild/helm/tooling/helm-pipelines'
file: '/.config-lint.yaml'
ref: main
- project: 'guilds1/cloud-native-guild/helm/tooling/helm-pipelines'
file: '/.helm.yaml'
- project: 'guilds1/cloud-native-guild/helm/tooling/helm-pipelines'
file: '/.kind.yaml'
ref: main
variables:
CHART: ${CI_PROJECT_NAME}
IMAGE_HELM_CHART_LINT: "quay.io/helmpack/chart-testing:v3.3.1"
IMAGE_TEST_DOCS: "renaultdigital/helm-docs:v1.5.0"
stages:
- pretest
- validation
- lint
- test
- build
- make_release
- publish
- integration
7- Let's run the pipeline and validate the rules.
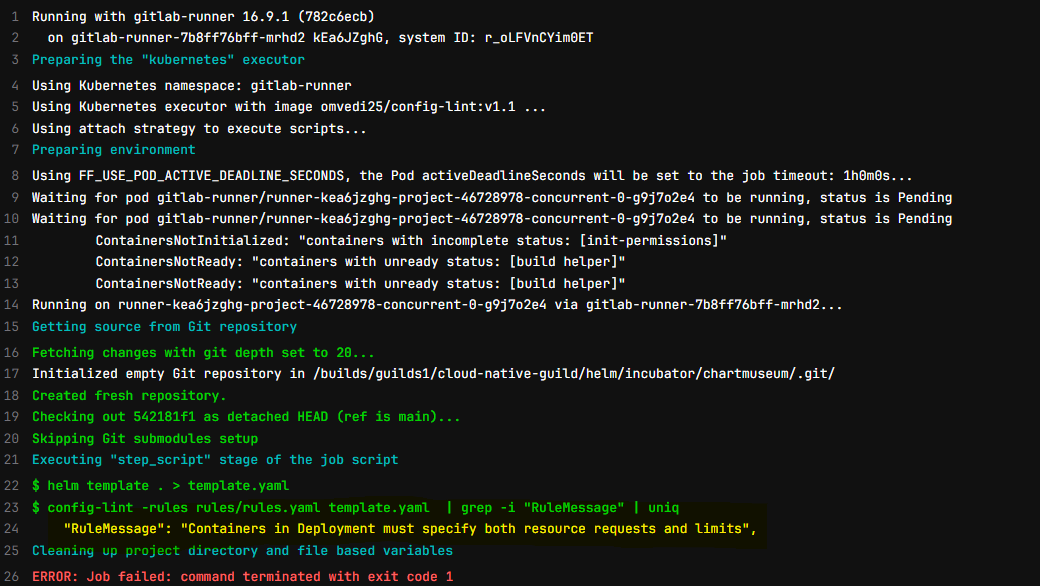
**We can see rules are working as expected. We can write our custom rules according to requirement to validate the charts with mandatory options **
Other Examples
# wget https://github.com/stelligent/config-lint/blob/master/example-files/rules/kubernetes.yml
# cat kubernetes.yml