Introduction to KubeArmor KubeArmor is an open-source security solution designed specifically for Kubernetes environments. Developed by AhnLab, a leading cybersecurity company, KubeArmor provides fine-grained container-aware security policies to enforce access control, system call filtering, and network policies.
Architecture Overview
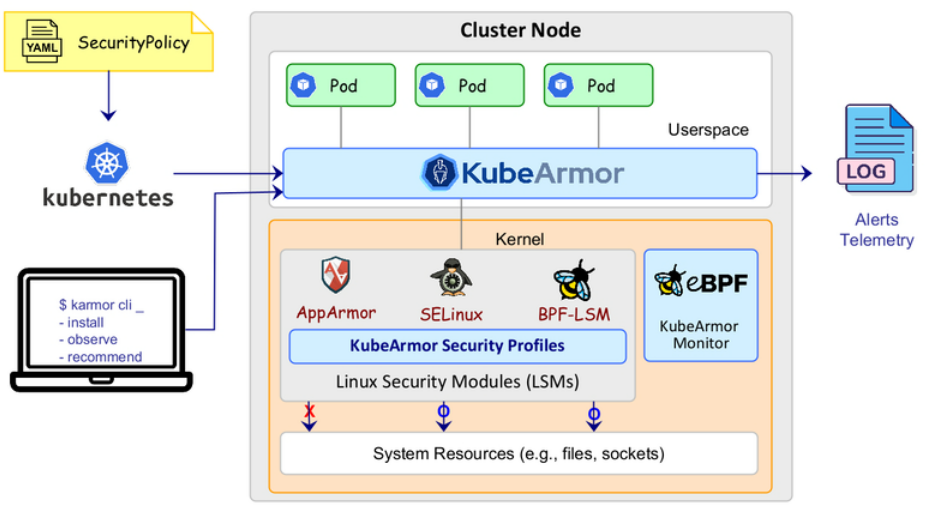
The Need for Kubernetes Security As organizations increasingly adopt Kubernetes for their containerized workloads, ensuring the security of these environments becomes crucial. Traditional security measures are often inadequate in containerized environments due to their dynamic nature and the large attack surface they present. KubeArmor addresses these challenges by providing granular security controls tailored to Kubernetes deployments.
Key Features of KubeArmor
Container-Aware Security Policies: KubeArmor allows administrators to define security policies at the container level, ensuring that each workload operates within its designated security context.
System Call Filtering: By intercepting and filtering system calls made by containers, KubeArmor can prevent unauthorized actions and enforce security policies in real-time.
Network Policies: KubeArmor enables administrators to define network policies to control inbound and outbound traffic between containers, helping to prevent lateral movement and unauthorized access.
Audit Logging: KubeArmor logs all security-related events, providing administrators with visibility into container activities and potential security threats.
How KubeArmor Works KubeArmor operates by deploying an agent as a DaemonSet within the Kubernetes cluster. This agent intercepts system calls made by containers and enforces security policies defined by the administrator. By leveraging the Linux Security Module (LSM) framework, KubeArmor integrates seamlessly with the underlying operating system, ensuring minimal performance overhead.
Install kubearmor
root@master:~# curl -sfL http://get.kubearmor.io/ | sudo sh -s -- -b /usr/local/bin
kubearmor/kubearmor-client info checking GitHub for latest tag
kubearmor/kubearmor-client info found version: 1.2.1 for v1.2.1/linux/amd64
kubearmor/kubearmor-client info installed /usr/local/bin/karmor
root@master:~# karmor install
🛡 Installed helm release : kubearmor-operator
😄 KubeArmorConfig created
⌚️ This may take a couple of minutes
ℹ️ Waiting for KubeArmor Snitch to run: —
Verify the Installation
root@master:~# kubectl get all -n kubearmor
NAME READY STATUS RESTARTS AGE
pod/kubearmor-apparmor-containerd-98c2c-6k2mc 1/1 Running 0 44m
pod/kubearmor-apparmor-containerd-98c2c-hhgww 1/1 Running 0 3m19s
pod/kubearmor-apparmor-containerd-98c2c-m2974 1/1 Running 0 45m
pod/kubearmor-controller-575b4b46c5-jnppw 2/2 Running 0 3m10s
pod/kubearmor-operator-5bcfb76b4f-8kkwp 1/1 Running 0 47m
pod/kubearmor-relay-6b59fbf77f-wqp7r 1/1 Running 0 46m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubearmor ClusterIP 10.97.110.240 <none> 32767/TCP 46m
service/kubearmor-controller-metrics-service ClusterIP 10.103.151.164 <none> 8443/TCP 46m
service/kubearmor-controller-webhook-service ClusterIP 10.111.41.204 <none> 443/TCP 46m
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
daemonset.apps/kubearmor-apparmor-containerd-98c2c 3 3 3 3 3 kubearmor.io/btf=yes,kubearmor.io/enforcer=apparmor,kubearmor.io/runtime=containerd,kubearmor.io/seccomp=yes,kubearmor.io/socket=run_containerd_containerd.sock,kubernetes.io/os=linux 45m
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/kubearmor-controller 1/1 1 1 46m
deployment.apps/kubearmor-operator 1/1 1 1 47m
deployment.apps/kubearmor-relay 1/1 1 1 46m
NAME DESIRED CURRENT READY AGE
replicaset.apps/kubearmor-controller-575b4b46c5 1 1 1 3m10s
replicaset.apps/kubearmor-controller-64b5b9d54b 0 0 0 46m
replicaset.apps/kubearmor-operator-5bcfb76b4f 1 1 1 47m
replicaset.apps/kubearmor-relay-6b59fbf77f 1 1 1 46m
Deploy nginx app in default namespace
root@master:~# kubectl create deployment nginx --image=nginx
deployment.apps/nginx created
root@master:~# kubectl get pods
NAME READY STATUS RESTARTS AGE
nginx-748c667d99-qjjxn 1/1 Running 0 34s
root@master:~# POD=$(kubectl get pod -l app=nginx -o name)
root@master:~# echo $POD
pod/nginx-748c667d99-qjjxn
Use Case: Deny Installation of package Management Tool Creating a policy to deny the execution
root@master:~# cat <<EOF | kubectl apply -f -
apiVersion: security.kubearmor.com/v1
kind: KubeArmorPolicy
metadata:
name: block-pkg-mgmt-tools-exec
spec:
selector:
matchLabels:
app: nginx
process:
matchPaths:
- path: /usr/bin/apt
- path: /usr/bin/apt-get
action:
Block
EOF
kubearmorpolicy.security.kubearmor.com/block-pkg-mgmt-tools-exec created
Lets Verify installing package
root@master:~# kubectl exec -it $POD -- bash -c "apt update && apt install masscan"
bash: line 1: /usr/bin/apt: Permission denied
command terminated with exit code 126
Use Case: Deny Access to Service Token To mitigate the risk posed by default service account tokens being mounted in every pod, even if not utilized by applications, you can restructure your Kubernetes cluster's service account setup. Policy to restrict access
root@master:~# cat <<EOF | kubectl apply -f -
apiVersion: security.kubearmor.com/v1
kind: KubeArmorPolicy
metadata:
name: block-service-access-token-access
spec:
selector:
matchLabels:
app: nginx
file:
matchDirectories:
- dir: /run/secrets/kubernetes.io/serviceaccount/
recursive: true
action:
Block
EOF
kubearmorpolicy.security.kubearmor.com/block-service-access-token-access created
Verify the service token access
root@nginx-748c667d99-qjjxn:/# kubectl exec -it $POD -- bash
root@nginx-748c667d99-qjjxn:/# curl https://$KUBERNETES_PORT_443_TCP_ADDR/api --insecure --header "Authorization: Bearer $(cat /run/secrets/kubernetes.io/serviceaccount/token)"
cat: /run/secrets/kubernetes.io/serviceaccount/token: Permission denied
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "forbidden: User \"system:anonymous\" cannot get path \"/api\"",
"reason": "Forbidden",
"details": {},
"code": 403
Use Case: Least Permission Policy
root@master:~# kubectl annotate ns default kubearmor-file-posture=block --overwrite
namespace/default annotated
root@master:~# cat <<EOF | kubectl apply -f -
apiVersion: security.kubearmor.com/v1
kind: KubeArmorPolicy
metadata:
name: only-allow-nginx-exec
spec:
selector:
matchLabels:
app: nginx
file:
matchDirectories:
- dir: /
recursive: true
process:
matchPaths:
- path: /usr/sbin/nginx
- path: /bin/bash
action:
Allow
EOF
kubearmorpolicy.security.kubearmor.com/only-allow-nginx-exec created
Verify the Access
root@master:~# kubectl exec -it $POD -- bash -c "chroot"
bash: line 1: /usr/sbin/chroot: Permission denied
command terminated with exit code 126
Benefits of Using KubeArmor Enhanced Security Posture: By enforcing fine-grained security policies at the container level, KubeArmor reduces the attack surface and mitigates the risk of unauthorized access and data breaches.
Compliance and Auditing: KubeArmor's audit logging capabilities help organizations demonstrate compliance with regulatory requirements and industry standards by providing detailed records of security-related events.
Operational Efficiency: With KubeArmor, administrators can centrally manage security policies across their Kubernetes clusters, streamlining security operations and reducing manual overhead.
Conclusion In today's threat landscape, securing Kubernetes environments is paramount for organizations seeking to harness the benefits of containerization without compromising on security. KubeArmor offers a robust solution for enhancing Kubernetes security by providing fine-grained security controls tailored to containerized workloads. By leveraging KubeArmor's capabilities, organizations can mitigate security risks, achieve compliance, and ensure the integrity of their Kubernetes deployments.
