Introduction In today's cloud-centric world, securely managing identities and access control is crucial. Azure DevOps is a powerful tool that helps automate deployment pipelines, but managing credentials securely can be challenging. One way to improve security and simplify management is by using Managed Identity for Azure resources. This blog will guide you through setting up a federated account to connect Azure DevOps to Azure using Service Connections via Managed Identity.
What is Managed Identity? Managed Identity is a feature of Azure Active Directory (Azure AD) that provides Azure services with an automatically managed identity. This identity can be used to authenticate to any service that supports Azure AD authentication, eliminating the need for managing credentials.
Why Use Managed Identity with Azure DevOps?
Security: Eliminates the need to store secrets in Azure DevOps, reducing the risk of credential leakage.
Simplification: Managed identities are automatically managed, so there's no need to rotate or manage keys.
Scalability: Easily manage access across multiple environments and projects without hardcoding credentials.
Step 1: Create a Managed Identity in Azure
Assign a Managed Identity to your Azure resource:
Navigate to the Azure portal. https://portal.azure.com
Go to the resource you want to enable a Managed Identity
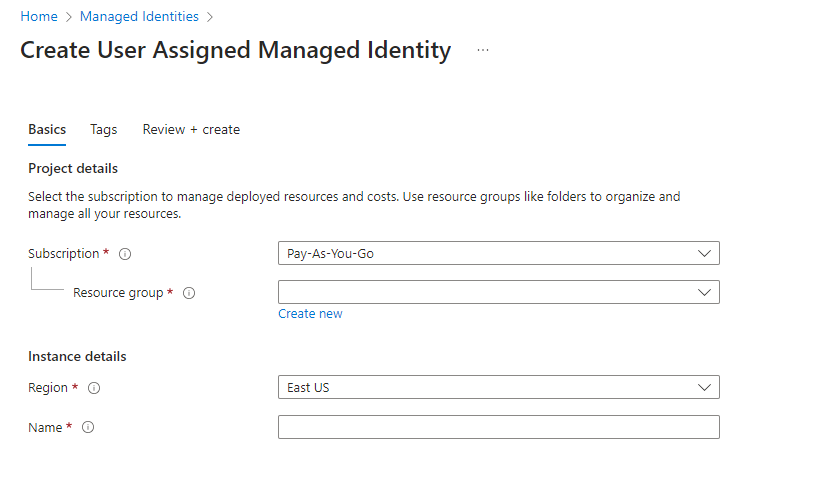
Click on Create New
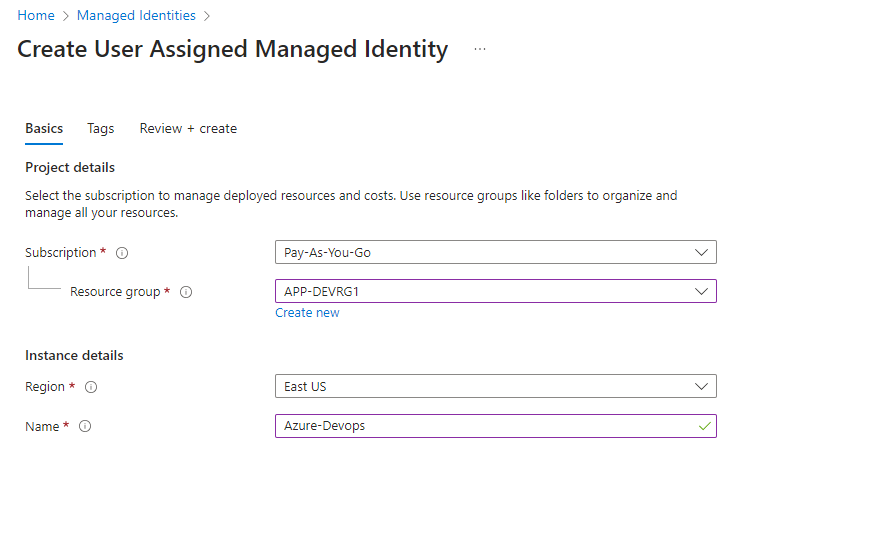
Select Resource Group and assign name, review and create
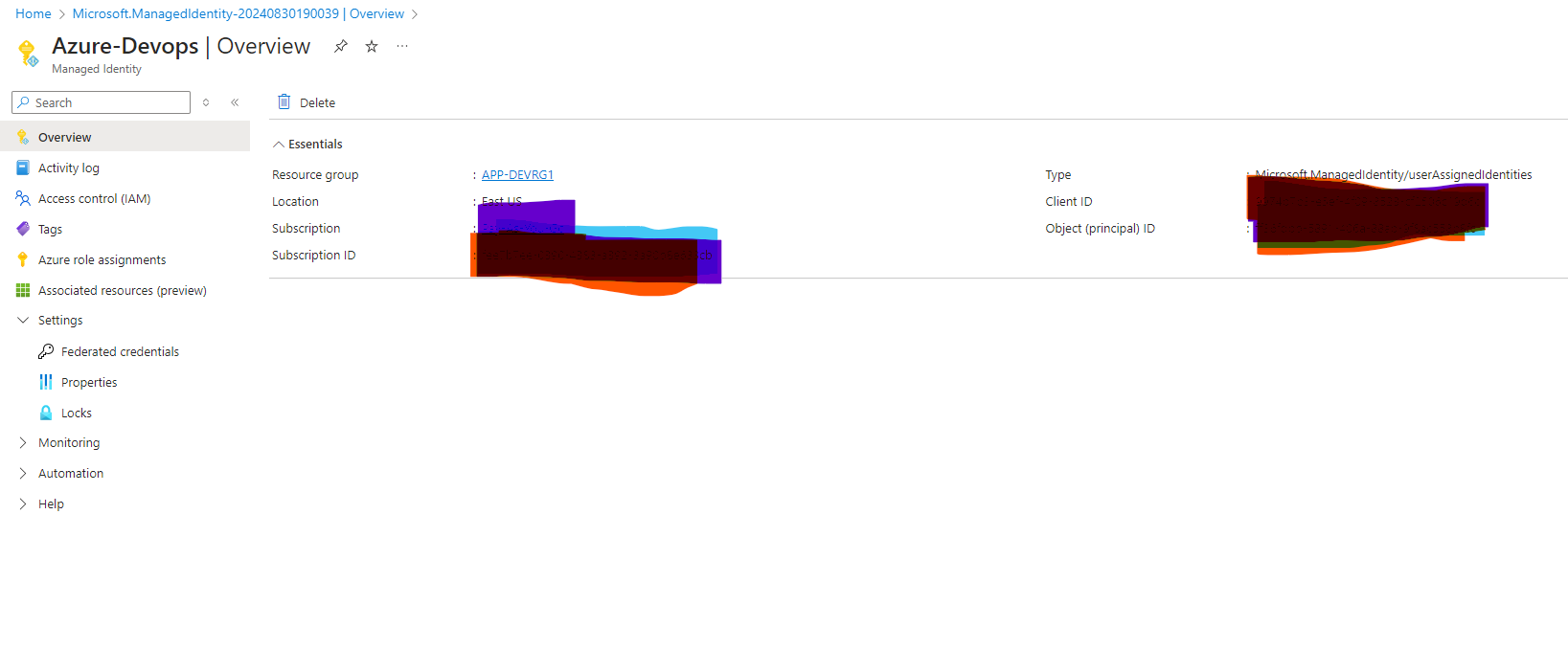
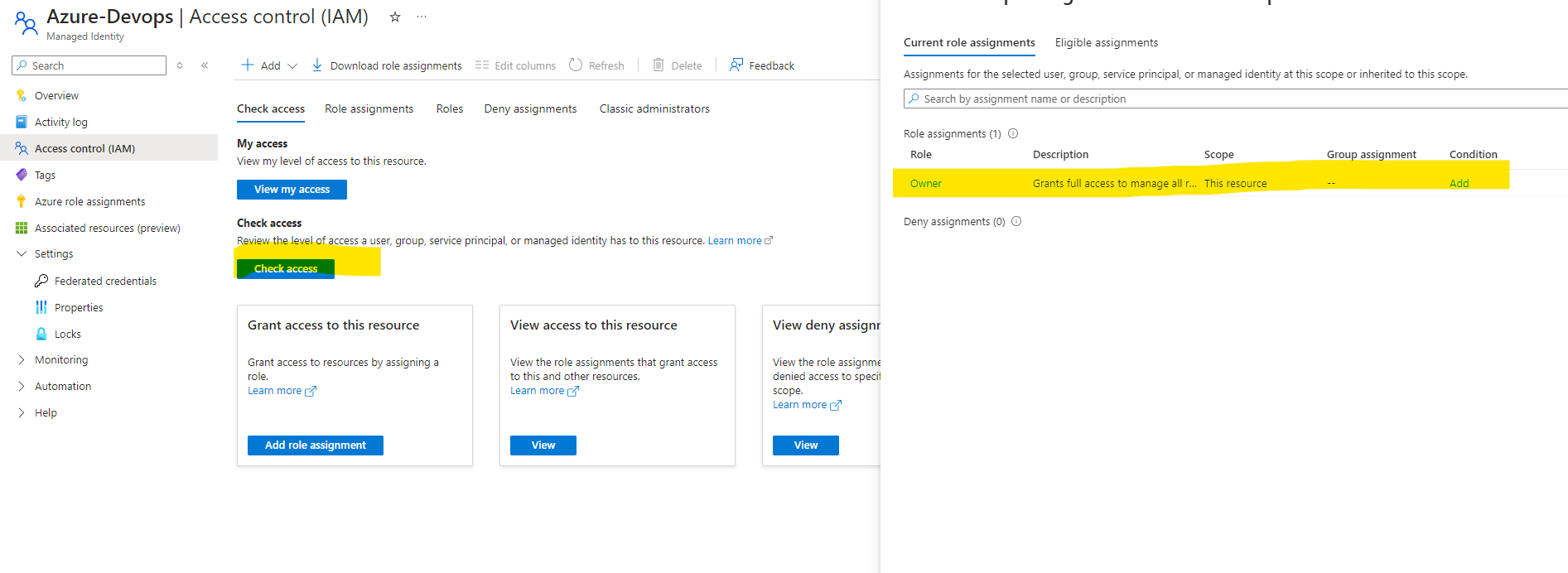
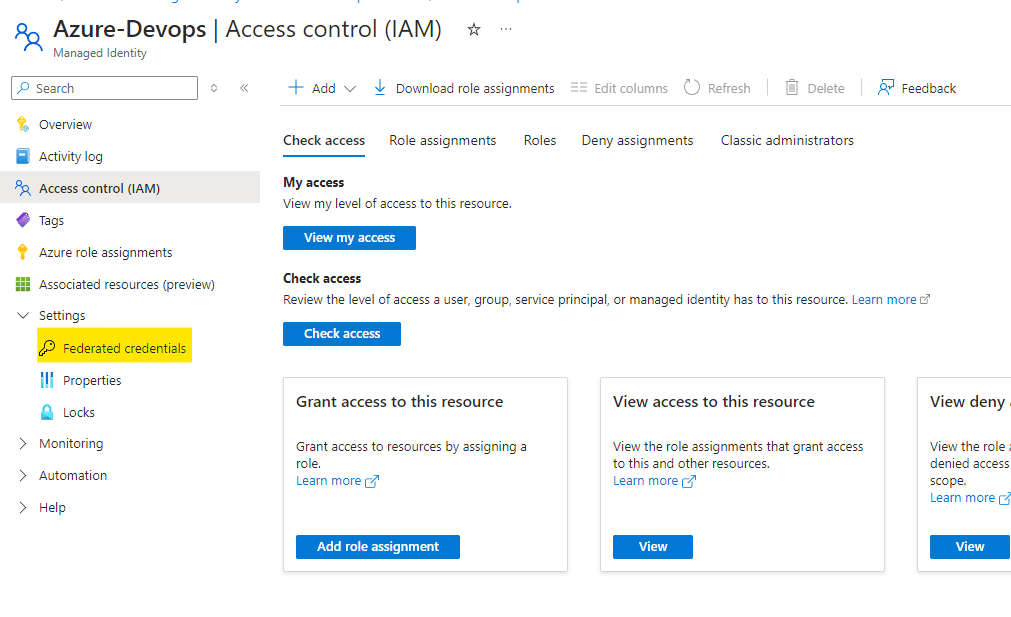
Click On Manage Identity and click on Access Control, Click on Add. Assign Role
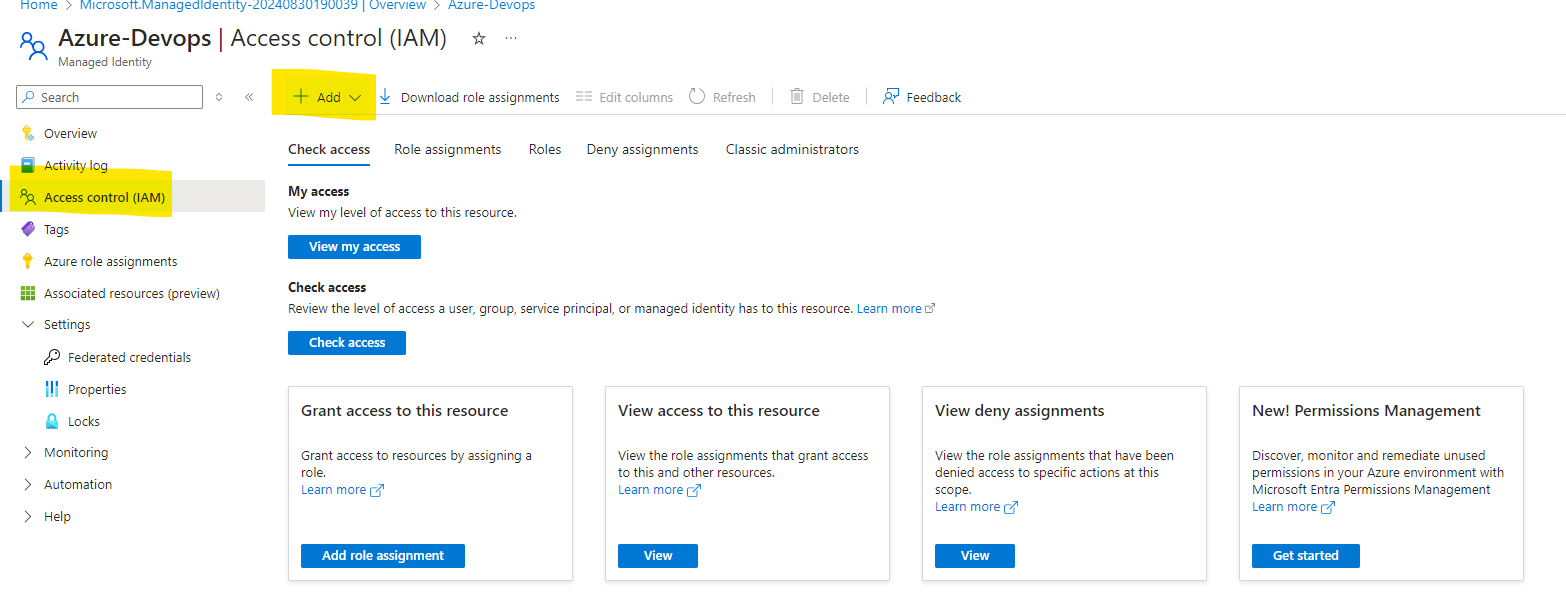
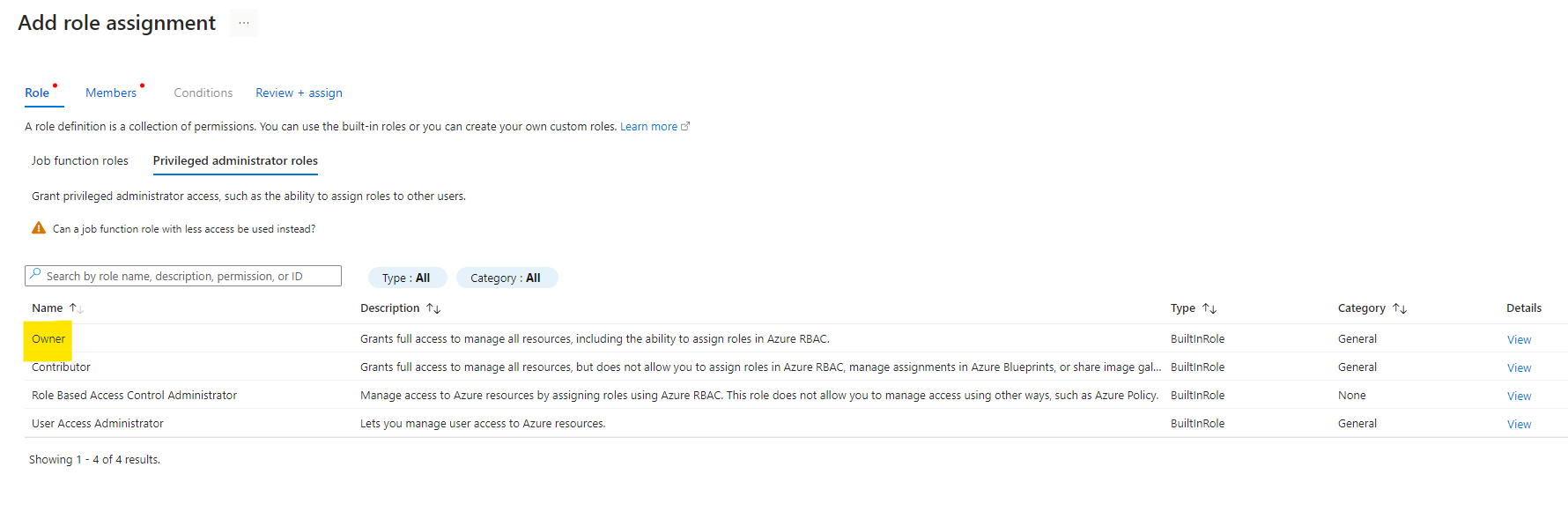
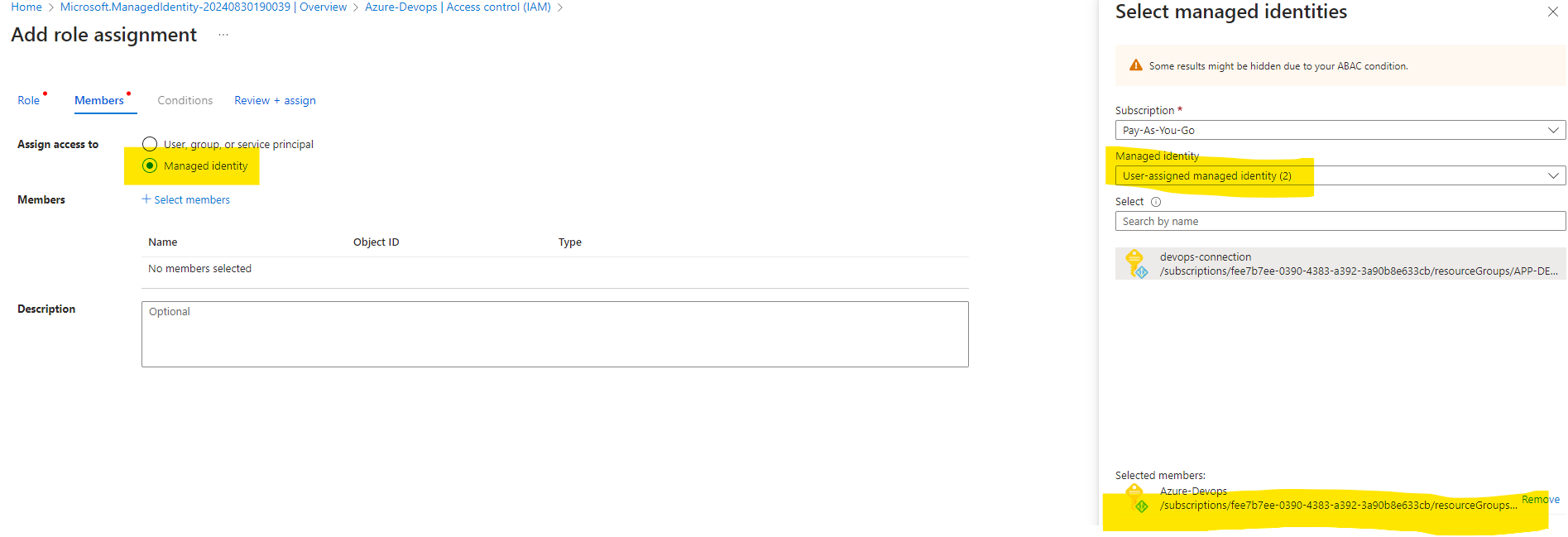
Review and Create
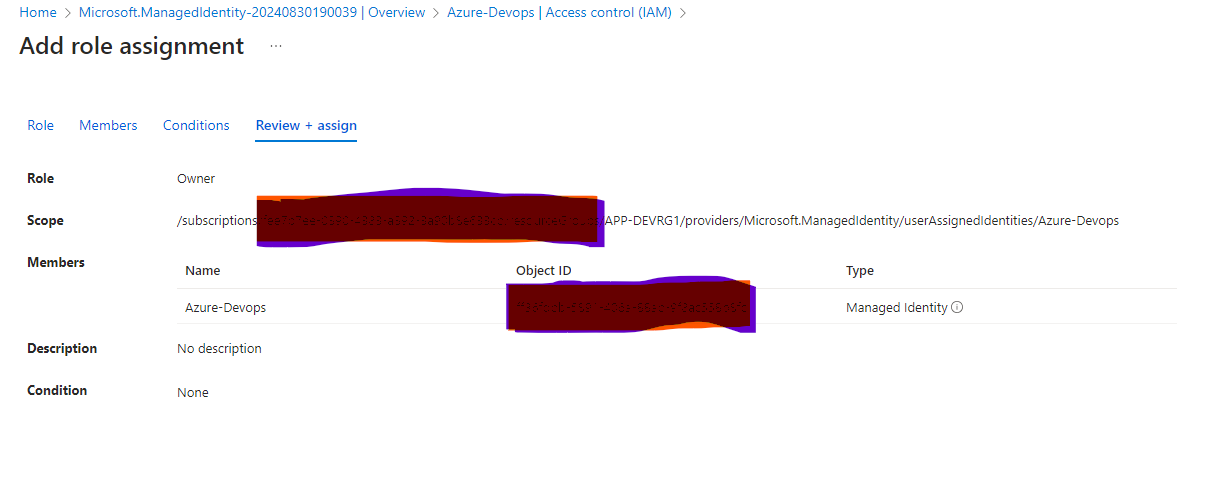
Review the access as we have assigned the Manage identity as Owner
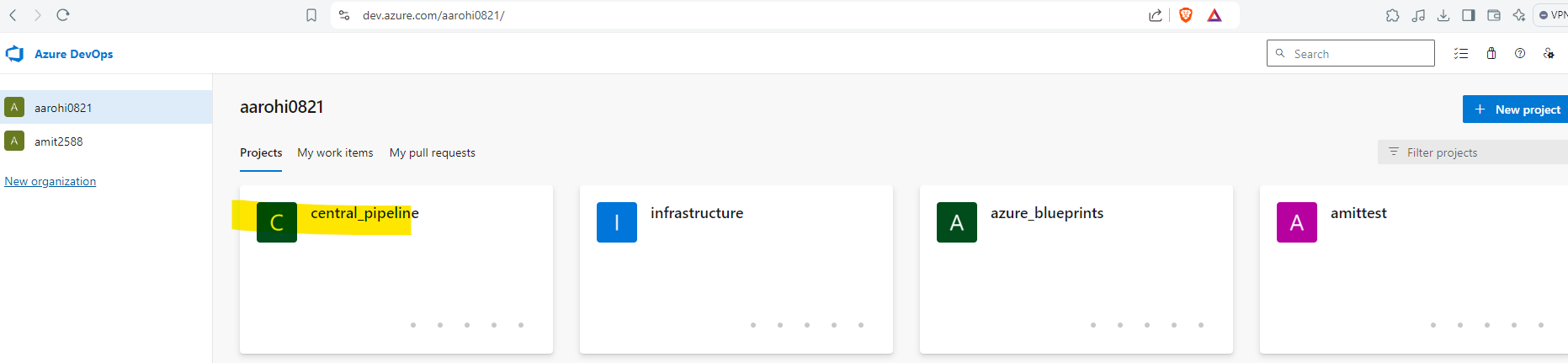
Login To Azure Devops and move to Your Project to Create Service Connection
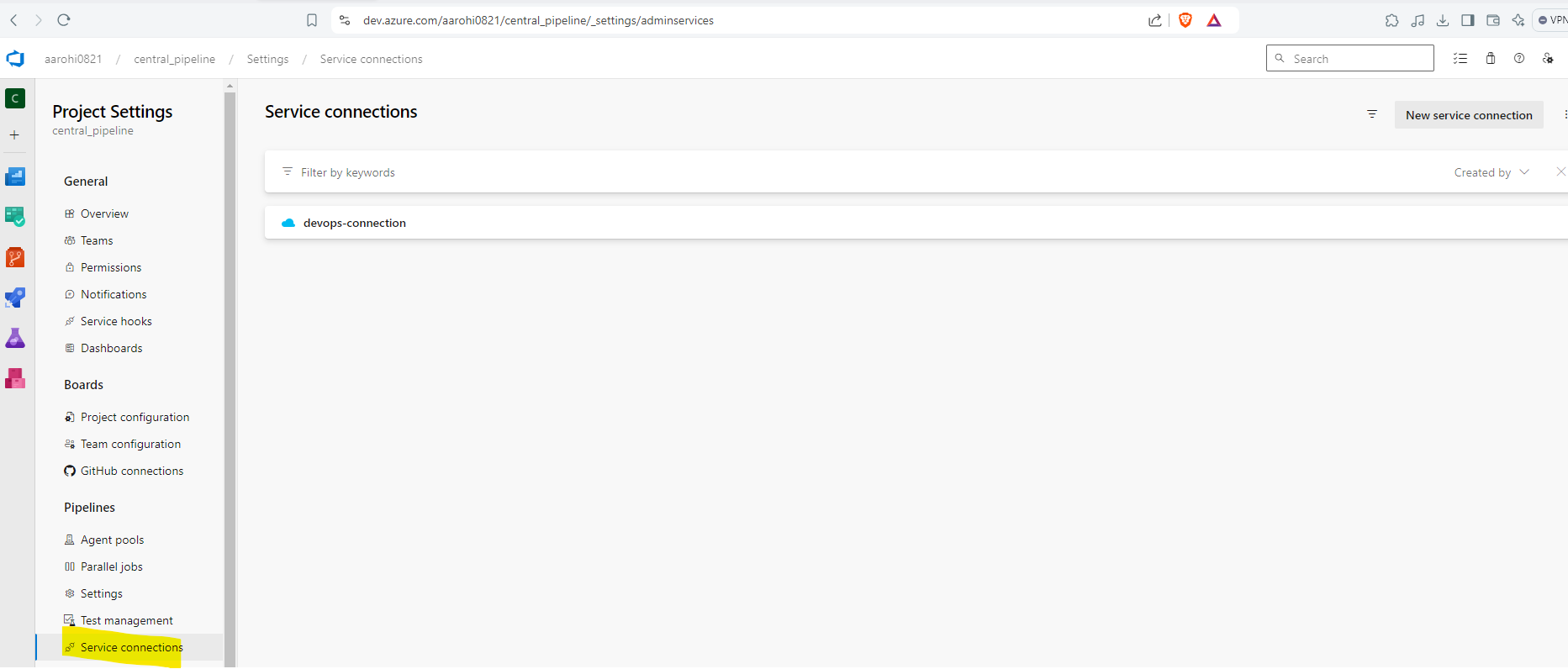
Click On Project Setting and Select Service Connection
Click On New Service Connection
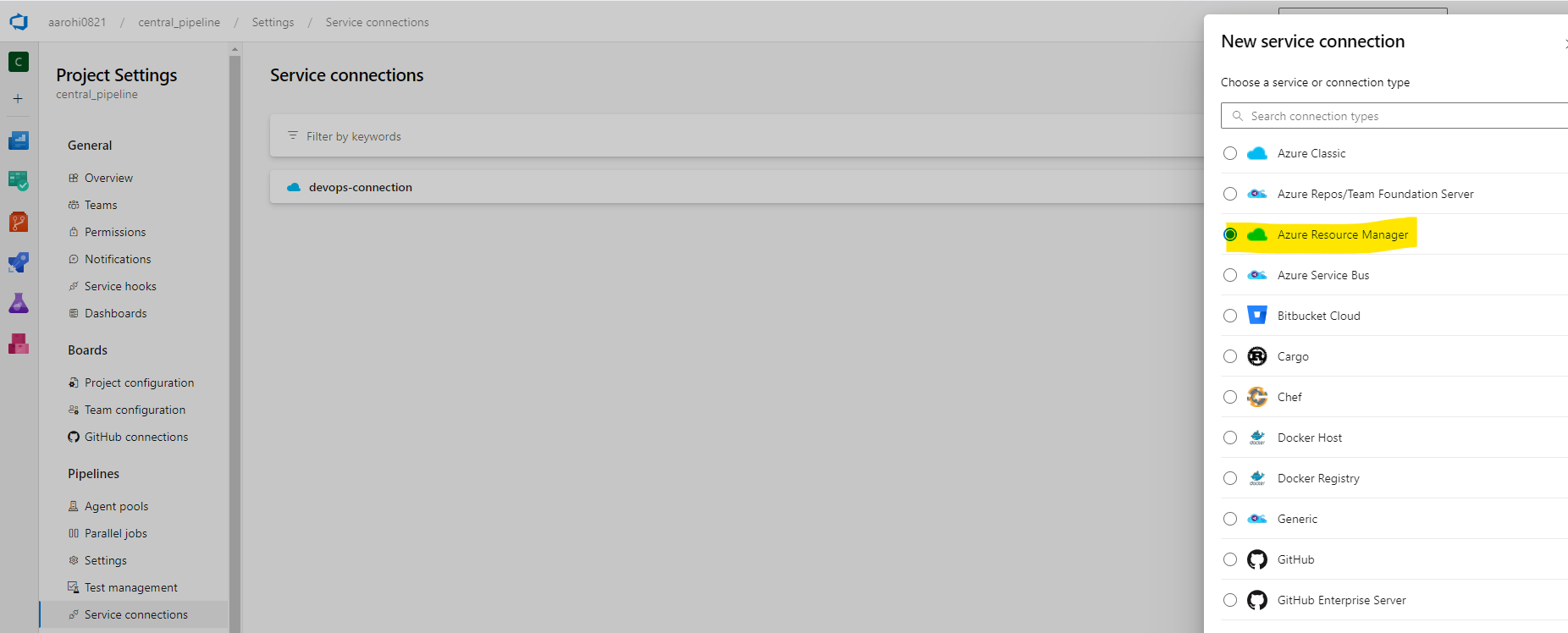
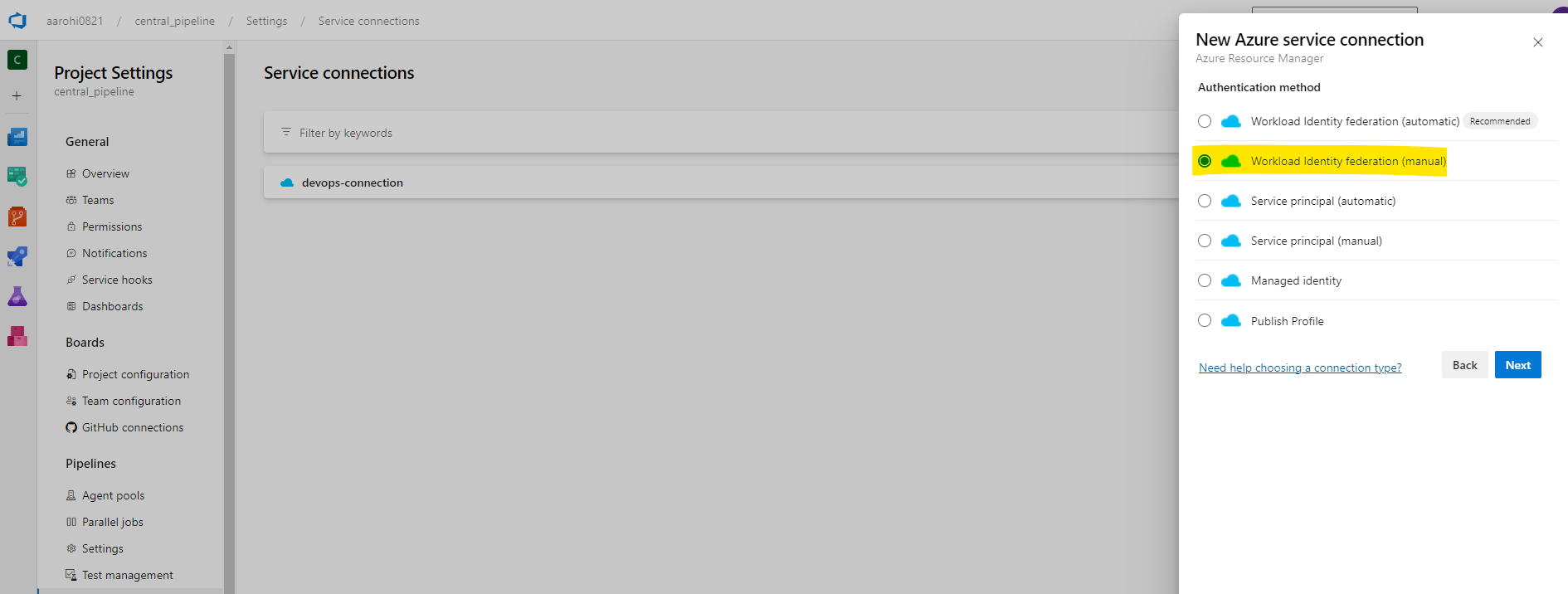
Give Connection Name and Description
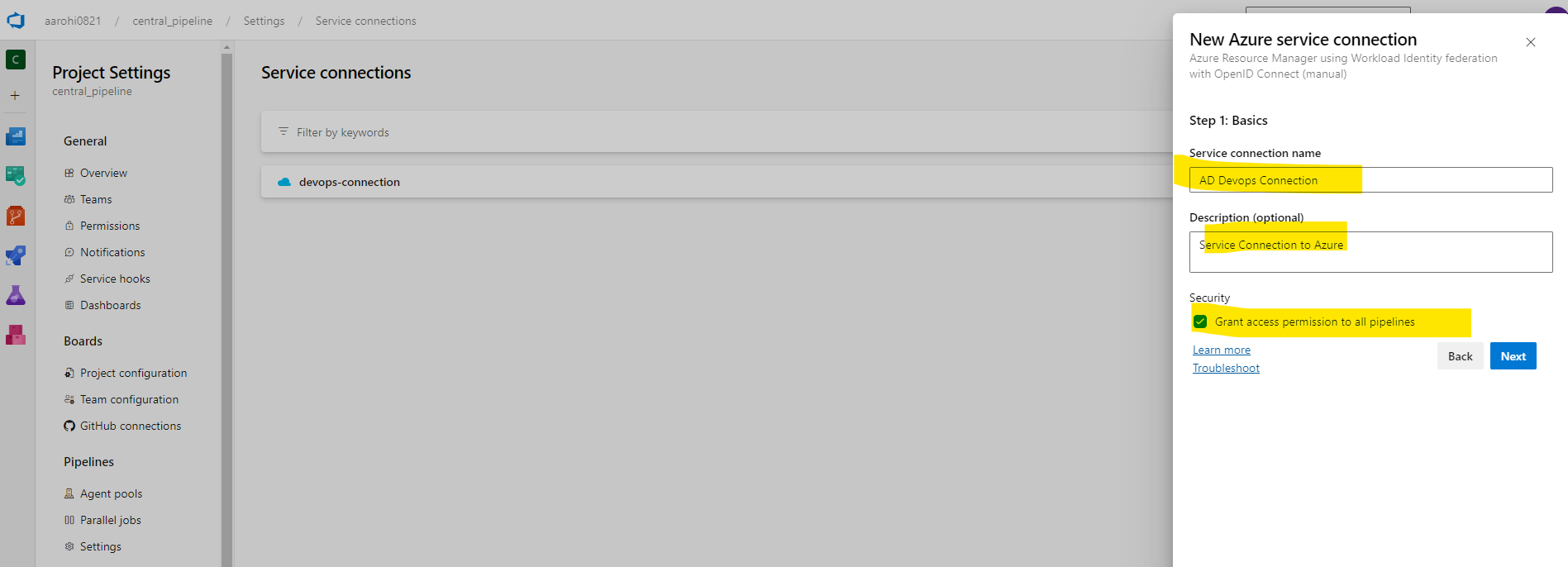
Click on Next and Collect Issuer Details, subject identifier and Keep in Notepad
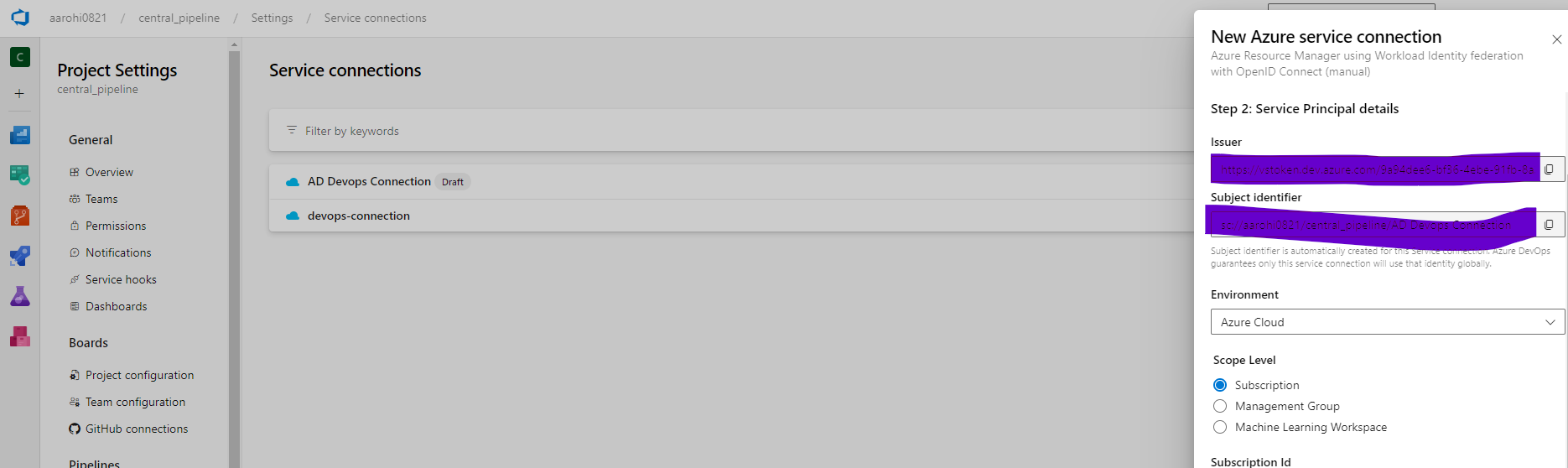
Provide Subscription Details for the Created Manage Identity
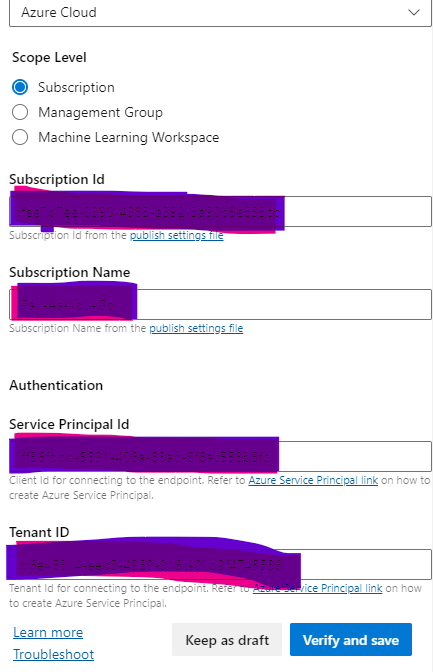
Login Back to Azure Portal and Select App Registration
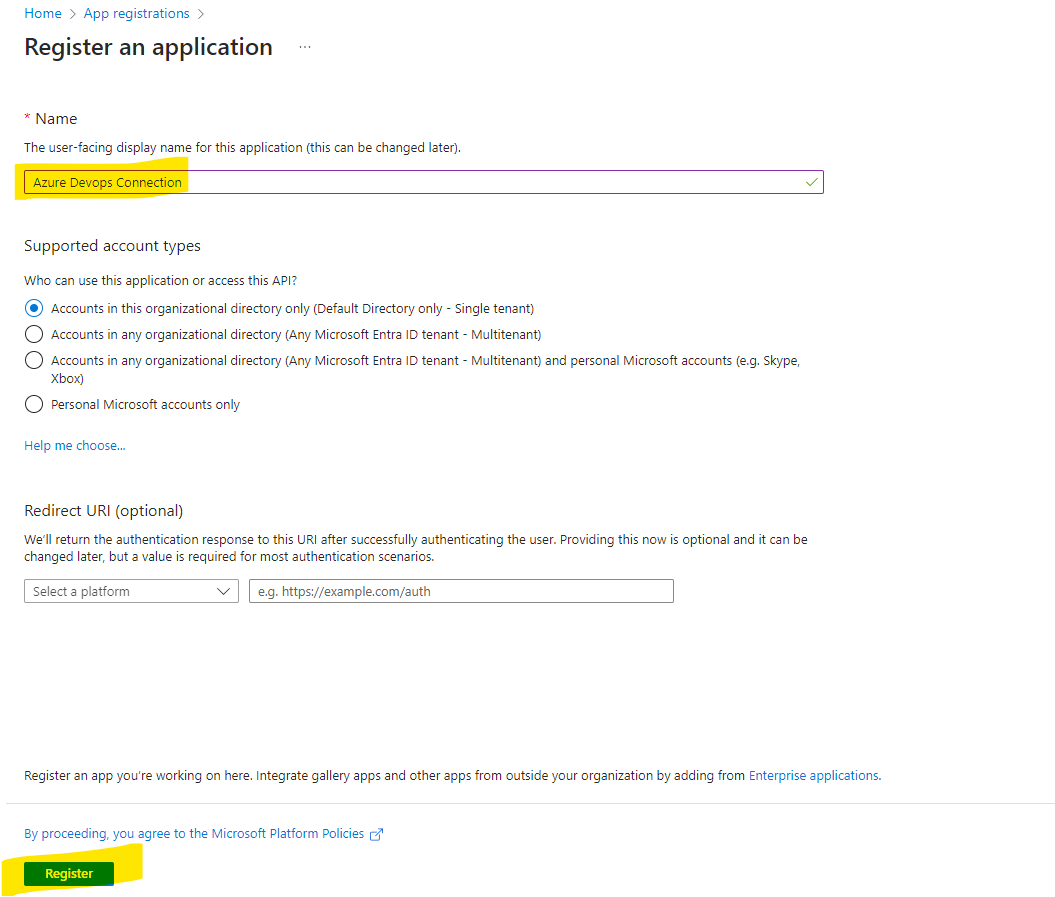
Create A new app registration and register it
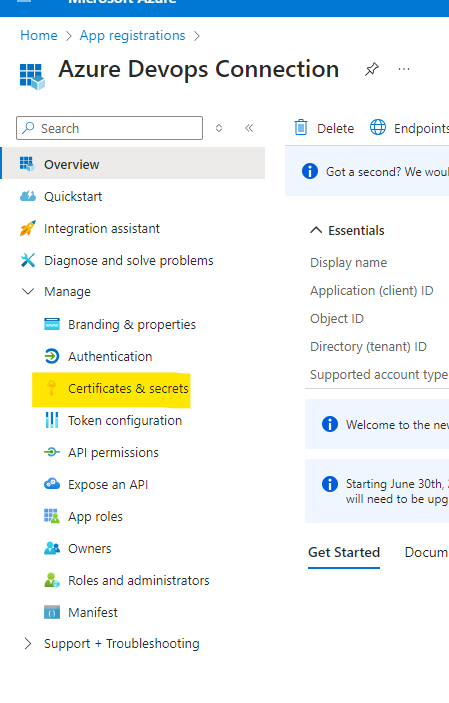
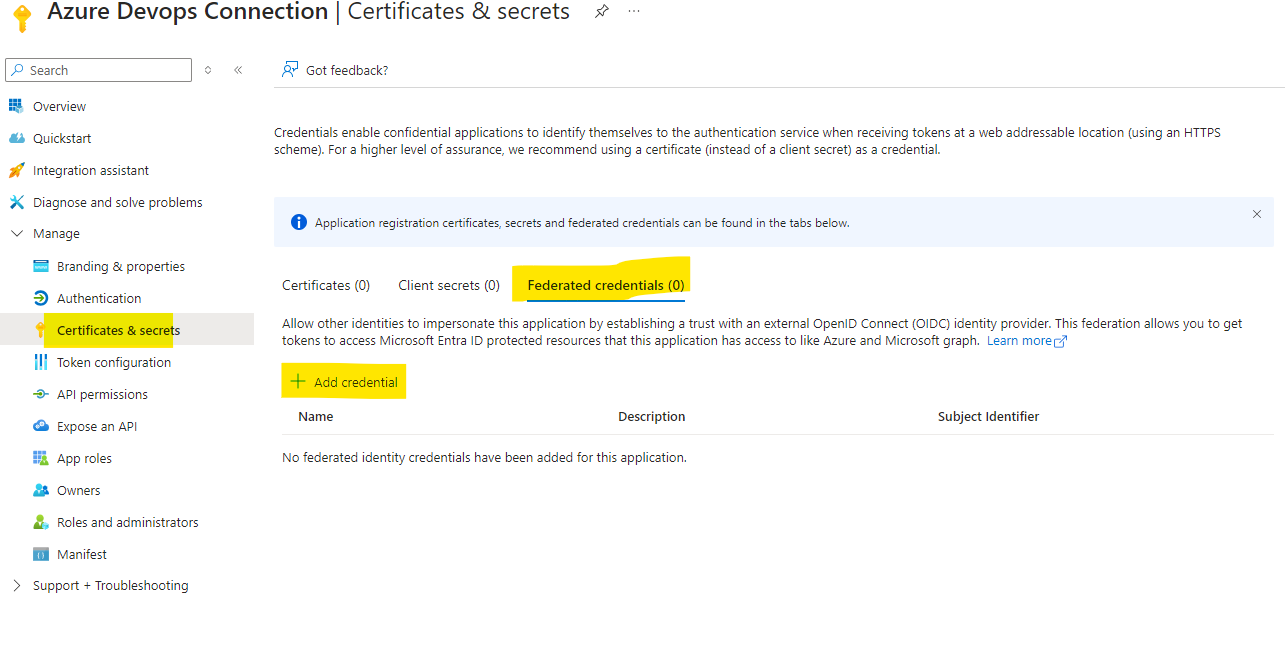
Select Certificate $ Secrets and Select Federated Credentials
Select Add Credentials
Provide the Issuer and Subject Identifier Created in Azure Devops Portal Service Connection
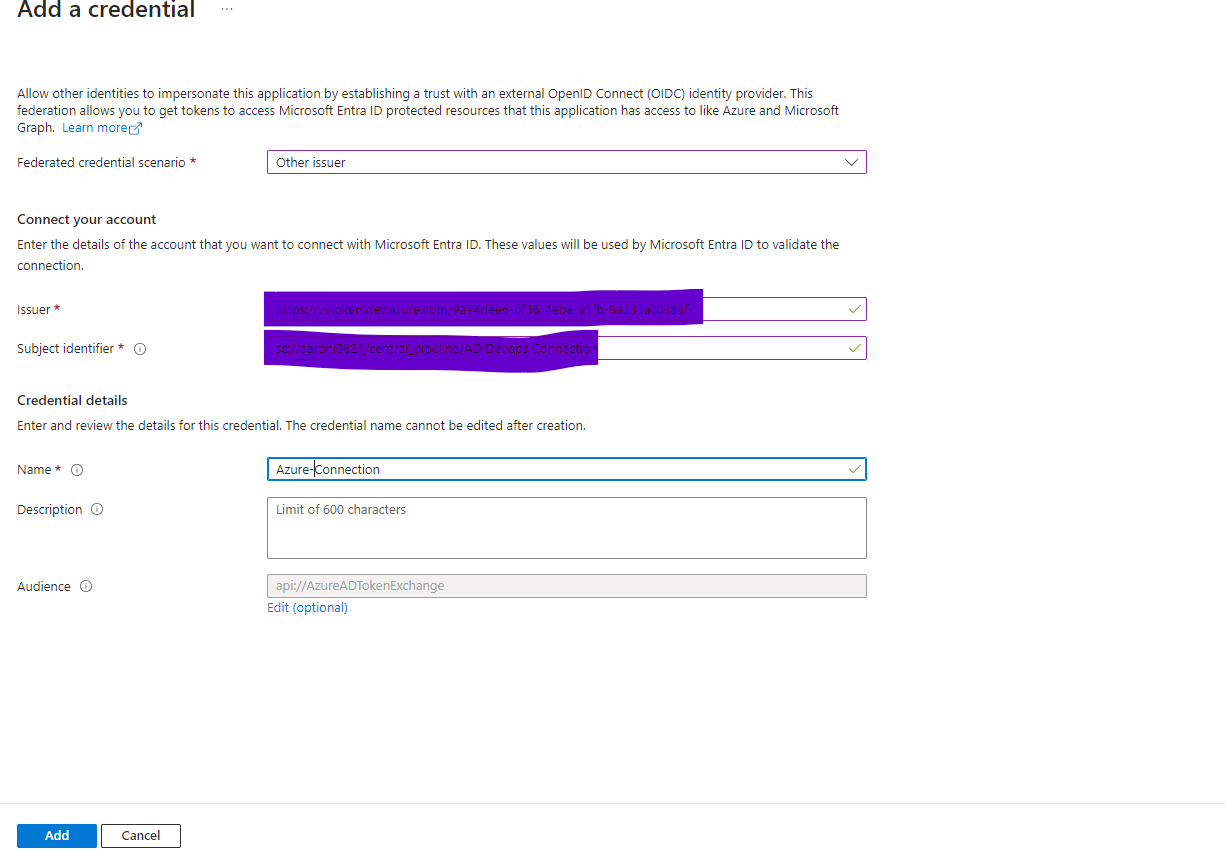
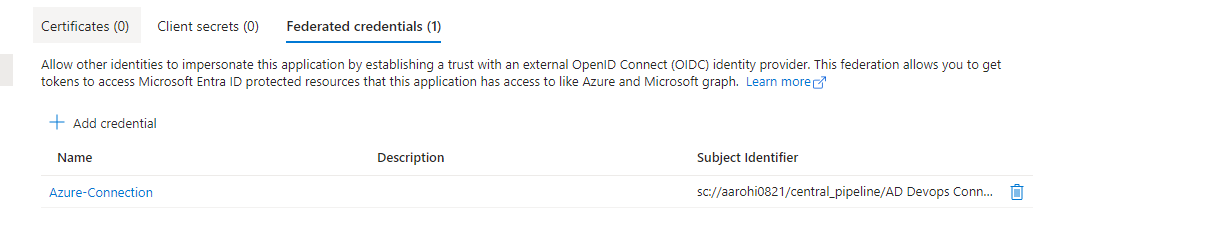
Select Created Manage Identity and select Federated Credential and click add credentials
Select Federated Scenario as other and provide Issuer, Subject Identifier and in credential Details name as Federated name created in app registration

Go Back to Azure Devops Portal, Service connection and click on Verify and Save
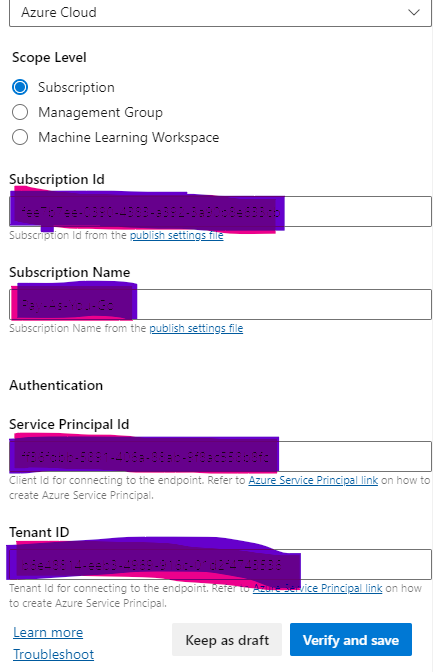
If Configuration Are proper connection will be saved
To verify the connection, lets create azure pipeline in the project
trigger:
- main
pool:
acloudguru
steps:
- task: AzureCLI@2
displayName: 'devops-connection'
inputs:
azureSubscription: 'devops-connection' # Use the correct service connection
scriptType: 'bash'
scriptLocation: 'inlineScript'
inlineScript: |
echo "Assigning role......."
az group create --name myResourceGroup --location eastus
Run the pipeline to deploy resources securely using the Managed Identity
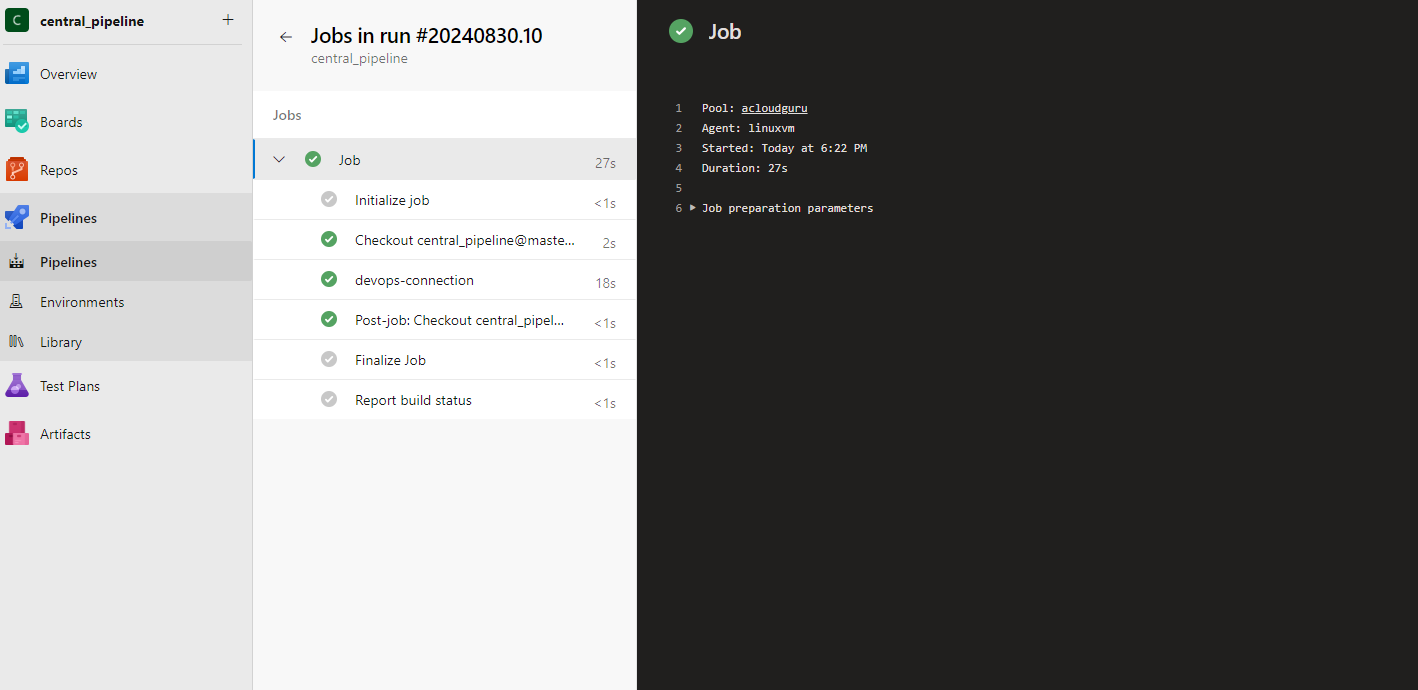
Conclusion Using Managed Identity to connect Azure DevOps to Azure resources provides a secure, scalable, and easy-to-manage way of handling authentication. This approach eliminates the need to store and manage secrets, which enhances security and simplifies operations. By leveraging federated identity credentials, you can further streamline and secure your CI/CD pipelines, making your deployments more robust and secure.
